I have figured out how to remove the whitelist from most (all) Insyde BIOSes. I used the F.34 BIOS for a Compaq Presario C700 series for this how to. You will need the EzH2O and WinHex tools. Using these tools I was able to figure out the byte that needed to be changed to ignore the PCIe wireless whitelist altogether. After not being able to find my subsys codes, I started looking around a bit. I found the 104 - Unsupported wireless network device detected string in the memory dump and the Microsoft EXE signature just above which lead to the breakthrough (at least for me). What follows is a general procedure to allow you to modify your own BIOS safely (I hope).
1. obtain your bios.fd file obtained from HP (or whatever manufacturer)
2. use Insyde BIOS editor - EZH2O (I used EZH20 2.1.0.4)
3. run exh2o.exe, open the file bios.fd
4. run WINHEX
5. Tools -> OpenRAM -> Ezh2o -> Entire Memory
6. Find HEX Values -> «31 00 30 00 34 00 2d 00 55», this should be the be the first part of the '104-U...' error string in wide character format (2 bytes/char) see step1.jpg.

7. from here search up and find HEX values «4d 5a», you can just scroll up a few pages till you see 'MZ' in the ASCII pane. This is the code that MS uses for start of an EXE. Somewhere between here and the 104 string is where we need to find and modify the JNZ (byte code 75)
8. You will notice that there is a lot of blank space around and below the 'MZ', this is header information and is of no interest. Scroll down till the ASCII pane no longer is mostly blanks, about a page, you should see «55 8b ec», this is the start of the program and is setting up the stack
9. Now click on the 55 and drag the mouse down to the next 'MZ' code about 1-2 pages on my BIOS, and then click Edit -> Copy Block -> Into New File and name the file Something.com. The .com is important as we will load it with debug. Refer to step2.jpg.

10. Open a command prompt and navigate to where you saved the file and type debug something.com, you should get a '-' prompt, type u and hit enter and you should see something like this. See step3.jpg.
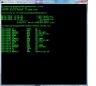
The first column is memory addresses, the 2nd column is instruction bytes and the rest are Intel mnemonics.
11. Now we need some elementary assembly skills to find what we are looking for. Debug will show the mnemonics for the instructions. Debug doesn't handle 386 instructions well so you may see a few ??? but we should be able to find what we need. Look for a test al,al followed by a jnz {address}. The unassemble should have addresses on the left and they should correspond to the addresses in the debug so you can then -u {address} to see what happens at the jump to locations. See step4.jpg.

12. Now that we know what to change write down a about 6 or so of the bytes ending with the 75 and the following byte (27 in the step 4 example) and go back to WinHex and from the start of our program (the «55 8b ec» bytes) search for the bytes you recorded. Make sure everything around matches your debug window and replace 75 (JNZ short) with eb (JMP short). eb is an unconditional jump and will exit the routine so we don't get to the infinite loop. See step5.jpg.

13. In WinHex save your change by clicking on the disk icon
14. Switch to EzH2O, File -> Save AS
15. Put your modified BIOS (and only that BIOS) where the flash utility can find it and start InsydeFlash and let it do it's thing.
16. Sometimes after flashing the machine may appear bricked but turn it off remove power and battery and then reapply power and turn it on. If it still doesn't come up Google for the procedure to use a USB memory stick to get your computer back. Might be a good idea to prepare the flash drive before you flash your BIOS.
Mark
1. obtain your bios.fd file obtained from HP (or whatever manufacturer)
2. use Insyde BIOS editor - EZH2O (I used EZH20 2.1.0.4)
3. run exh2o.exe, open the file bios.fd
4. run WINHEX
5. Tools -> OpenRAM -> Ezh2o -> Entire Memory
6. Find HEX Values -> «31 00 30 00 34 00 2d 00 55», this should be the be the first part of the '104-U...' error string in wide character format (2 bytes/char) see step1.jpg.
7. from here search up and find HEX values «4d 5a», you can just scroll up a few pages till you see 'MZ' in the ASCII pane. This is the code that MS uses for start of an EXE. Somewhere between here and the 104 string is where we need to find and modify the JNZ (byte code 75)
8. You will notice that there is a lot of blank space around and below the 'MZ', this is header information and is of no interest. Scroll down till the ASCII pane no longer is mostly blanks, about a page, you should see «55 8b ec», this is the start of the program and is setting up the stack
9. Now click on the 55 and drag the mouse down to the next 'MZ' code about 1-2 pages on my BIOS, and then click Edit -> Copy Block -> Into New File and name the file Something.com. The .com is important as we will load it with debug. Refer to step2.jpg.
10. Open a command prompt and navigate to where you saved the file and type debug something.com, you should get a '-' prompt, type u and hit enter and you should see something like this. See step3.jpg.
The first column is memory addresses, the 2nd column is instruction bytes and the rest are Intel mnemonics.
11. Now we need some elementary assembly skills to find what we are looking for. Debug will show the mnemonics for the instructions. Debug doesn't handle 386 instructions well so you may see a few ??? but we should be able to find what we need. Look for a test al,al followed by a jnz {address}. The unassemble should have addresses on the left and they should correspond to the addresses in the debug so you can then -u {address} to see what happens at the jump to locations. See step4.jpg.
12. Now that we know what to change write down a about 6 or so of the bytes ending with the 75 and the following byte (27 in the step 4 example) and go back to WinHex and from the start of our program (the «55 8b ec» bytes) search for the bytes you recorded. Make sure everything around matches your debug window and replace 75 (JNZ short) with eb (JMP short). eb is an unconditional jump and will exit the routine so we don't get to the infinite loop. See step5.jpg.
13. In WinHex save your change by clicking on the disk icon
14. Switch to EzH2O, File -> Save AS
15. Put your modified BIOS (and only that BIOS) where the flash utility can find it and start InsydeFlash and let it do it's thing.
16. Sometimes after flashing the machine may appear bricked but turn it off remove power and battery and then reapply power and turn it on. If it still doesn't come up Google for the procedure to use a USB memory stick to get your computer back. Might be a good idea to prepare the flash drive before you flash your BIOS.
Mark



![[-] [-]](https://www.bios-mods.com/forum/images/black/collapse.png)









![Validate my RSS feed [Valid RSS]](valid-rss.png)